Three years passed before Lo and Chau, and Mayers discovered the flaws of BCJL93, more or less simultaneously. The advances in quantum computing theory provided them with better formalisms on quantum physics and quantum computations and allowed them to frame the problem with a clearer perspective. Their papers were first published online ([16], [11]) and later appeared together on Physical Review Letters ([17], [12]). To prove that quantum bit commitment is impossible, a general structure or scheme of a QBC protocol is needed, encompassing all possible such protocols. The authors at the time had doubts on the generality of the ones they had used. Lo and Chau's 1998 article [13] and review [7] have definitively settled the issue.6
The general idea of a protocol involves three quantum systems, one for Alice,
one for Bob, and one for a communications channel. According to quantum physics,
the state of each one of these is a unitary7 vector on a Hilbert8 space, so we must consider state spaces HA, HB, and HCfor each of this characters. The complete state of all of them put together
is a vector in the direct (tensor) product of the three, namely the space
![]() .
Note that in as much as quantum physics encompasses classical physics, this
is also a description for any classical (or mixed) protocol. The protocol will
require A and B to prepare and manipulate their states, which
involves computing and storage. Once again, from the point of view of quantum
physics, the most general description of these are quantum computers. The assumption
is, then, that A and B have a quantum computer each. With this
gadgets they are able to perform manipulations on their state-spaces, namely,
to rotate the state by any unitary transformation9.
.
Note that in as much as quantum physics encompasses classical physics, this
is also a description for any classical (or mixed) protocol. The protocol will
require A and B to prepare and manipulate their states, which
involves computing and storage. Once again, from the point of view of quantum
physics, the most general description of these are quantum computers. The assumption
is, then, that A and B have a quantum computer each. With this
gadgets they are able to perform manipulations on their state-spaces, namely,
to rotate the state by any unitary transformation9.
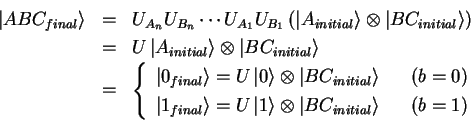
After the commitment phase, the entire system is in one of two states: Either
the state originating from an initial b=0, which will be called
![]() or the one generated from b=1, namely,
or the one generated from b=1, namely,
![]() .
Since all the protocol is known to both parties, they both know the entire matrix
U of the whole computation process, the only difference being that Bignores what the initial state of HA was.
.
Since all the protocol is known to both parties, they both know the entire matrix
U of the whole computation process, the only difference being that Bignores what the initial state of HA was.
The key element at this point is that B must get no information whatsoever
on what the value of b is. So both states
![]() and
and
![]() must look identical from his
point of view. This said in mathematical terms, the trace with respect to HAof the observable associated with
must look identical from his
point of view. This said in mathematical terms, the trace with respect to HAof the observable associated with
![]() is identical
to that of
is identical
to that of
![]() .
We do this with a tool called
Schmidt decomposition[7]: there are bases
.
We do this with a tool called
Schmidt decomposition[7]: there are bases ![]() of HAand
of HAand
![]() of HBC , and numbers
of HBC , and numbers
![]() such that
such that
and the trace taken to bring the observable
![]() down to HBC yields11
down to HBC yields11
Similarly, there are bases
![]() of HA and
of HA and
![]() of HBC, and scalars
of HBC, and scalars
![]() such that
such that
and
But since B cannot tell between each other, it must be the case that
for all i,
![]() and
and
![]() .
The only difference between the states lies inside HA which means
now that A can manipulate it at will! This is the problem that ruins
the whole setup. Alice does not need to have access to HBC in order
to cheat. Here's what she should do:
.
The only difference between the states lies inside HA which means
now that A can manipulate it at will! This is the problem that ruins
the whole setup. Alice does not need to have access to HBC in order
to cheat. Here's what she should do: